Major Cloud Providers Mitigate Massive DDoS Attacks Exploiting HTTP/2 Protocol Flaw

Amazon Web Services (AWS), Cloudflare, and Google disclosed this week that they mitigated record-breaking distributed denial-of-service (DDoS) attacks in late August 2023 that exploited a novel technique called HTTP/2 Rapid Reset.
The layer seven attacks peaked at 398 million requests per second (RPS) against Google’s infrastructure, over 155 million RPS on AWS, and 201 million RPS on Cloudflare. The attack vector is tracked as CVE-2023-44487 with a CVSS severity score of 7.5 out of 10.
HTTP/2 Rapid Reset is a zero-day vulnerability in the HTTP/2 protocol leveraged to overwhelm targets with DDoS floods. A key HTTP/2 feature is multiplexing requests over a single TCP connection via concurrent streams.
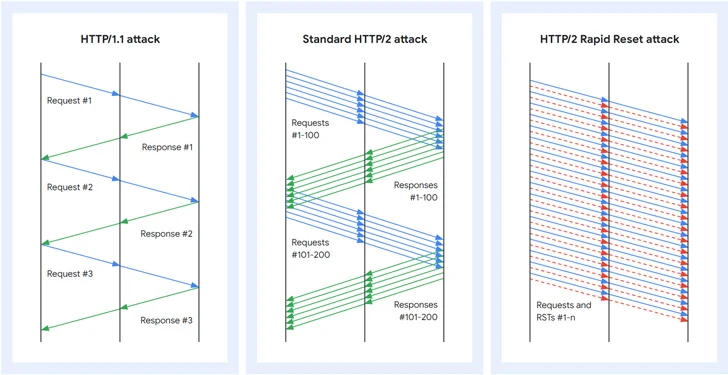
Clients can abort streams by sending RST_STREAM frames. The Rapid Reset attack exploits this to open rapidly and immediately reset streams, circumventing server limits on concurrent streams and overloading servers without exceeding configured thresholds.
AWS explained that “HTTP/2 rapid reset attacks consist of multiple HTTP/2 connections with requests and resets in quick succession, generating significant log traffic from requests that are then abruptly canceled.”
This indefinite number of in-flight requests on each connection allows massive HTTP/2 request floods that can cripple websites by saturating their capacity to handle new requests. By aggressively opening and resetting hundreds of thousands of streams at scale, attackers can take sites offline despite using relatively small botnets.
Cloudflare CSO Grant Bourzikas noted, “This zero-day provided threat actors with a powerful new DDoS technique to attack victims at an unprecedented scale.”
With HTTP/2 used by over 35% of websites and 77% of requests, the vulnerability poses a significant threat. Variants observed by Google are more efficient than standard HTTP/2 DDoS attacks.
F5 recommended configuration changes like limiting concurrent streams to mitigate attacks. Cloudflare urged rapid patching before exploits become widespread. The coordinated disclosure indicates major providers are acting to protect customers against disastrous impacts.