Blind Eagle Targets Colombian Insurance Sector with Customized Quasar RAT
The Colombian insurance sector has become the latest target of a sophisticated threat actor known as Blind Eagle. Since June 2024, this advanced persistent threat (APT) group has been deploying a customized version of the well-known Quasar Remote Access Trojan (RAT) to infiltrate organizations within the industry. The campaign represents a significant escalation in Blind Eagle’s activities, demonstrating their evolving tactics and persistent focus on South American entities.
Threat Actor Profile
Blind Eagle, also identified by aliases such as AguilaCiega, APT-C-36, and APT-Q-98, has a notorious history of targeting organizations and individuals across South America. Their operations predominantly focus on government and financial sectors in Colombia and Ecuador. The group’s activities are characterized by sophisticated phishing campaigns, malware customization, and the strategic use of compromised infrastructure to evade detection.
Initial Attack Vector
According to a recent analysis by Zscaler ThreatLabz researcher Gaetano Pellegrino, the attacks begin with phishing emails that impersonate the Colombian tax authority. Pellegrino noted, “Attacks have originated with phishing emails impersonating the Colombian tax authority.” These emails are meticulously crafted to appear legitimate, exploiting the trust recipients place in governmental communications.
Phishing Campaign Details
The phishing emails are designed to create a sense of urgency and fear. Blind Eagle achieves this by sending notifications that falsely claim the recipient is subject to a seizure order due to outstanding tax payments. Pellegrino explained, “The lure used by Blind Eagle involved sending a notification to the victim, claiming to be a seizure order due to outstanding tax payments. This is intended to create a sense of urgency and pressure the victim into taking immediate action.”
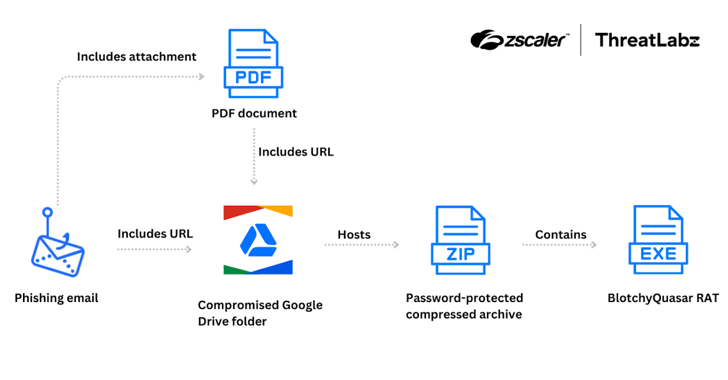
The emails contain malicious links, either embedded within a PDF attachment or directly in the email body. These links lead to ZIP archives hosted on a Google Drive folder associated with a compromised account belonging to a regional government organization in Colombia. By leveraging legitimate platforms and compromised accounts, Blind Eagle increases the likelihood of recipients trusting and interacting with the malicious content.
Malware Deployment
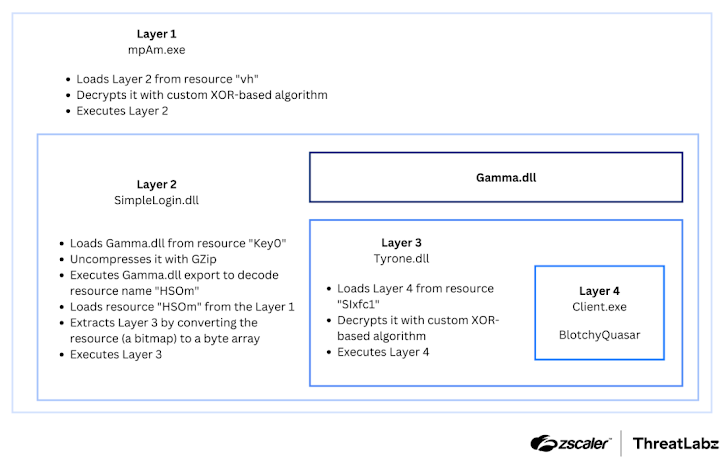
Once the victim downloads and opens the ZIP archive, they inadvertently execute a customized variant of the Quasar RAT, dubbed BlotchyQuasar. This variant is not the standard version; it includes additional layers of obfuscation using tools such as DeepSea and ConfuserEx. These obfuscation techniques are designed to hinder analysis and reverse engineering efforts by cybersecurity professionals.
Capabilities of BlotchyQuasar
The customized Quasar RAT variant possesses a wide array of malicious capabilities, including:
- Keystroke Logging: Capturing all keystrokes made by the victim, potentially revealing sensitive information such as passwords and confidential communications.
- Shell Command Execution: Allowing the attacker to run arbitrary commands on the infected system, effectively granting full control over the device.
- Data Theft: Extracting data from web browsers and FTP clients, including stored credentials and browsing history.
- Monitoring Financial Activities: Specifically targeting interactions with banking and payment services located in Colombia and Ecuador, which could facilitate financial fraud or further data theft.
Advanced Command-and-Control Techniques
Blind Eagle employs sophisticated methods to manage the compromised systems. They use Pastebin as a dead drop resolver to fetch the command-and-control (C2) domain. This technique involves storing the C2 domain information on Pastebin, which the malware retrieves upon execution. Additionally, the threat actors leverage Dynamic DNS (DDNS) services to host the C2 domain, enhancing their ability to change the C2 infrastructure rapidly and avoid detection.
Infrastructure Concealment
To shield their operations, Blind Eagle hides its infrastructure behind a combination of VPN nodes and compromised routers, primarily located in Colombia. Pellegrino remarked, “Blind Eagle typically shields its infrastructure behind a combination of VPN nodes and compromised routers, primarily located in Colombia. This attack demonstrates the continued use of this strategy.” This approach makes it challenging for defenders to trace the source of the attacks and dismantle the threat actor’s network.
Previous Documentation and Analysis
The attack chain and techniques used by Blind Eagle have been previously documented by cybersecurity firms such as Kaspersky and IBM X-Force. In July 2023, IBM X-Force detailed the use of BlotchyQuasar, highlighting the group’s ongoing efforts to customize and enhance their malware tools. Kaspersky’s analysis further shed light on the phishing tactics and the use of compromised government accounts to distribute malware.
Implications for the Colombian Insurance Sector
The targeted attacks against the Colombian insurance sector signify a strategic move by Blind Eagle to infiltrate critical financial infrastructure. Insurance companies handle vast amounts of sensitive personal and financial data, making them lucrative targets for cybercriminals. A successful breach could lead to significant financial losses, reputational damage, and the compromise of customer data.
Recommendations for Organizations
To mitigate the risks posed by Blind Eagle and similar threat actors, organizations, especially within the targeted sectors, should implement the following measures:
- Employee Training: Conduct regular cybersecurity awareness training to help employees recognize phishing emails and social engineering tactics.
- Email Security Solutions: Deploy advanced email filtering and threat detection systems to identify and block malicious emails before they reach end-users.
- Multi-Factor Authentication (MFA): Implement MFA across all critical systems to prevent unauthorized access, even if credentials are compromised.
- Regular Updates and Patching: Ensure all systems and software are up-to-date with the latest security patches to reduce vulnerabilities.
- Network Monitoring: Utilize intrusion detection and prevention systems to monitor for unusual network activity that may indicate a breach.
- Incident Response Planning: Develop and regularly update an incident response plan to quickly address and contain any security incidents.
Conclusion
Blind Eagle’s ongoing campaign against the Colombian insurance sector underscores the evolving nature of cyber threats in South America. By leveraging customized malware like BlotchyQuasar and sophisticated phishing tactics, the group continues to pose a significant risk to organizations within the region. It is imperative for targeted industries to remain vigilant, adopt robust cybersecurity practices, and collaborate with security researchers and authorities to defend against such advanced persistent threats.
About Blind Eagle
Blind Eagle is a cyber-espionage group with a focus on South American targets. Their activities are characterized by persistent targeting of government entities, financial institutions, and other high-value organizations. Their use of customized malware and advanced obfuscation techniques indicates a high level of sophistication and resources.
About Quasar RAT
Quasar RAT is an open-source remote access trojan that has been widely used by cybercriminals due to its availability and extensive capabilities. While originally intended for legitimate purposes, it has been repurposed by threat actors like Blind Eagle to facilitate unauthorized access and control over victim systems.
By understanding the methods and tools used by threat actors like Blind Eagle, organizations can better prepare and protect themselves against such sophisticated cyber attacks. Continuous monitoring, employee education, and adherence to cybersecurity best practices remain critical components in the fight against cybercrime.
