Experts Identify Three Chinese-Linked Cyberattack Clusters Targeting Southeast Asia
Cybersecurity experts have identified three threat activity clusters linked to China that have been compromising government organizations in Southeast Asia. This renewed state-sponsored operation, codenamed Crimson Palace, indicates an expansion in the scope of cyber espionage efforts in the region.
Discovery and Monitoring
The cybersecurity firm Sophos has been monitoring this cyber offensive, which comprises three intrusion sets:
- Cluster Alpha (STAC1248)
- Cluster Bravo (STAC1870)
- Cluster Charlie (STAC1305)
(Note: STAC stands for “Security Threat Activity Cluster.”)
According to Sophos security researchers Mark Parsons, Morgan Demboski, and Sean Gallagher, “The attackers consistently used other compromised organizational and public service networks in that region to deliver malware and tools under the guise of a trusted access point.”
Attack Methodology
A notable aspect of these attacks is the use of compromised systems from unnamed organizations as command-and-control (C2) relay points and staging grounds for malicious tools. A second organization’s compromised Microsoft Exchange Server was utilized to host malware, further obfuscating the attackers’ activities.
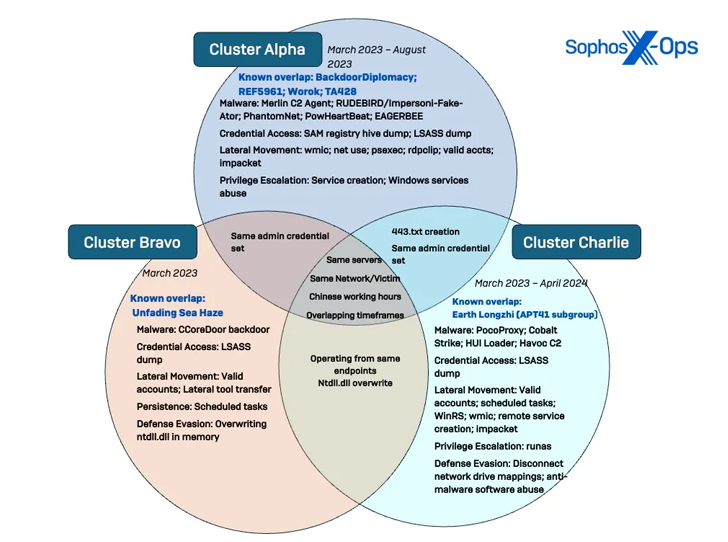
Crimson Palace was first documented by Sophos in early June 2024, with attacks occurring between March 2023 and April 2024. While initial activity associated with Cluster Bravo (also known as Unfading Sea Haze) was confined to March 2023, a new wave of attacks detected between January and June 2024 targeted 11 additional organizations and agencies in the region.
Expanded Targeting and Techniques
Further attacks orchestrated by Cluster Charlie (referred to as Earth Longzhi) were identified between September 2023 and June 2024. These attacks involved the deployment of different C2 frameworks such as Cobalt Strike, Havoc, and XieBroC2 to facilitate post-exploitation activities and deliver additional payloads like SharpHound for mapping Active Directory infrastructures.
The researchers noted, “Exfiltration of data of intelligence value was still an objective after the resumption of activity. However, much of their effort appeared to be focused on re-establishing and extending their foothold on the target network by bypassing EDR software and rapidly re-establishing access when their C2 implants had been blocked.”
Shared Tactics and Tools
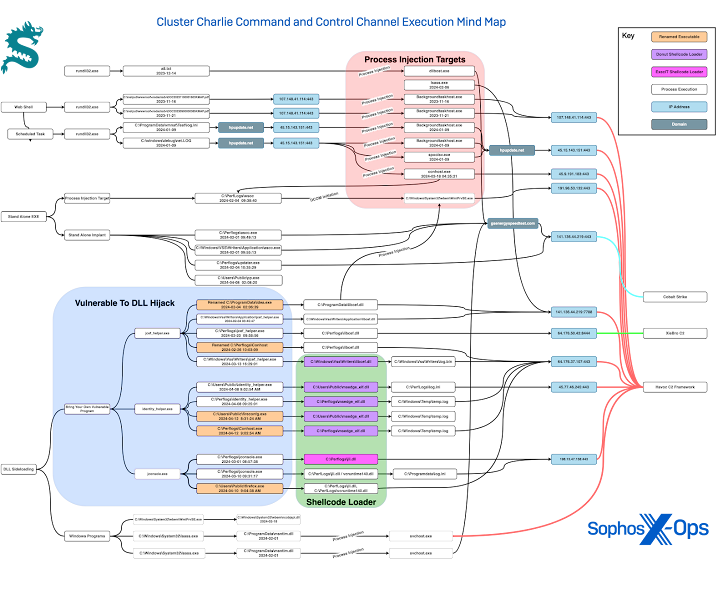
An important aspect of these clusters is Cluster Charlie’s heavy reliance on DLL hijacking to execute malware—an approach previously adopted by the threat actors behind Cluster Alpha. This suggests a “cross-pollination” of tactics among the groups.
Other open-source programs used by the threat actors include:
- RealBlindingEDR: Allows termination of antivirus processes.
- Alcatraz: Used for obfuscating portable executable files (.exe, .dll, .sys) to evade detection.
Additionally, a previously unknown keylogger dubbed TattleTale was identified in August 2023. This malware is capable of collecting browser data from Google Chrome and Microsoft Edge and can fingerprint compromised systems, check for mounted drives, collect domain controller names, and steal sensitive security information.
Collaborative Attack Chain
The three clusters appear to work in tandem, each focusing on specific tasks within the attack chain:
- Cluster Alpha: Infiltrating target environments and conducting reconnaissance.
- Cluster Bravo: Establishing deeper network penetration using various C2 mechanisms.
- Cluster Charlie: Exfiltrating valuable data.
Conclusion
“Throughout the engagement, the adversary appeared to continually test and refine their techniques, tools, and practices,” the researchers concluded. “As we deployed countermeasures for their bespoke malware, they combined the use of their custom-developed tools with generic, open-source tools often used by legitimate penetration testers, testing different combinations.”
The identification of these clusters underscores the persistent and evolving nature of cyber threats facing government organizations in Southeast Asia. It highlights the importance of robust cybersecurity measures and continuous monitoring to detect and mitigate advanced persistent threats.
About Sophos
Sophos is a global leader in next-generation cybersecurity, protecting organizations from today’s most advanced cyber threats. Through its extensive research and development efforts, Sophos provides real-time intelligence and tools to help organizations defend against sophisticated attacks.


