CosmicBeetle Deploys Custom ScRansom Ransomware in Collaboration with RansomHub

The threat actor known as CosmicBeetle has introduced a new custom ransomware strain called ScRansom, targeting small and medium-sized businesses (SMBs) across Europe, Asia, Africa, and South America. Evidence suggests that CosmicBeetle is also collaborating with the ransomware group RansomHub.
Replacement of Scarab with ScRansom
According to a recent analysis by ESET researcher Jakub Souček, CosmicBeetle has replaced its previously deployed Scarab ransomware with the continually improved ScRansom. Souček noted, “While not being top-notch, the threat actor is able to compromise interesting targets.” The sectors affected by ScRansom attacks include manufacturing, pharmaceuticals, legal services, education, healthcare, technology, hospitality, leisure, financial services, and regional government entities.
Background on CosmicBeetle
CosmicBeetle, also known as NONAME, is notorious for its malicious toolkit called Spacecolon, previously used to distribute the Scarab ransomware globally. The group has a history of experimenting with leaked ransomware builders, such as the LockBit builder, attempting to masquerade as more infamous ransomware gangs in their ransom notes and leak sites since November 2023.
Attribution Challenges
While the exact identity and origin of CosmicBeetle remain unclear, earlier hypotheses suggested a possible Turkish connection due to the use of a custom encryption scheme in a tool named ScHackTool. However, ESET now believes this attribution may no longer be valid. Souček explained, “ScHackTool’s encryption scheme is used in the legitimate Disk Monitor Gadget. It is likely that this algorithm was adapted from a Stack Overflow thread by VOVSOFT [a Turkish software firm], and years later, CosmicBeetle stumbled upon it and used it for ScHackTool.”
Attack Vectors and Techniques
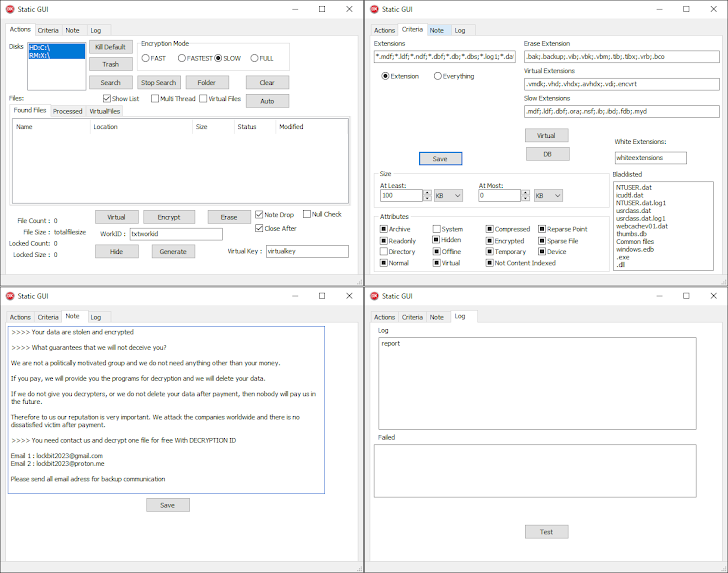
CosmicBeetle’s attack chains exploit brute-force methods and known security vulnerabilities, including CVE-2017-0144, CVE-2020-1472, CVE-2021-42278, CVE-2021-42287, CVE-2022-42475, and CVE-2023-27532, to infiltrate target environments. The group employs various tools like Reaper, Darkside, and RealBlindingEDR to terminate security processes and evade detection before deploying the Delphi-based ScRansom ransomware. ScRansom supports partial encryption to expedite the encryption process and features an “ERASE” mode that renders files unrecoverable by overwriting them with constant values.
Collaboration with RansomHub
The connection to RansomHub arises from observations by ESET of ScRansom and RansomHub payloads being deployed on the same machines within a short time frame. Souček stated, “Probably due to the obstacles that writing custom ransomware from scratch brings, CosmicBeetle attempted to leech off LockBit’s reputation, possibly to mask the issues in the underlying ransomware and in turn to increase the chance that victims will pay.”
Developments in the Ransomware Landscape
Cicada3301’s Updated Encryptor
Simultaneously, threat actors associated with the Cicada3301 ransomware, also known as Repellent Scorpius, have been using an updated version of their encryptor since July 2024. Palo Alto Networks Unit 42 reported that the new version includes a command-line argument --no-note, which, when invoked, prevents the encryptor from writing a ransom note to the system. Additionally, the latest variant no longer contains hard-coded usernames or passwords but retains the ability to execute PsExec using existing credentials.
Evolution of BURNTCIGAR (POORTRY)
Further developments include the evolution of a kernel-mode signed Windows driver known as POORTRY or BURNTCIGAR, used by multiple ransomware gangs to disable Endpoint Detection and Response (EDR) software. Delivered via a loader named STONESTOP, this malware orchestrates a Bring Your Own Vulnerable Driver (BYOVD) attack, bypassing Driver Signature Enforcement safeguards. Trend Micro first noted its ability to “force delete” files on disk in May 2023.
Sophos highlighted that both the Stonestop executable and the Poortry driver are heavily packed and obfuscated, using a closed-source packer named ASMGuard available on GitHub. POORTRY focuses on disabling EDR products by removing or modifying kernel notify routines, terminating security-related processes, and wiping critical files off disk.
Increased Use of EDR-Killer Tools
RansomHub’s use of an improved version of POORTRY, along with other EDR-killer tools like EDRKillShifter and legitimate software such as Kaspersky’s TDSSKiller, indicates an ongoing trend of ransomware groups experimenting with various methods to disable EDR products. Sophos commented, “It’s important to recognize that threat actors have been consistently experimenting with different methods to disable EDR products—a trend we’ve been observing since at least 2022.”
Conclusion
The activities of CosmicBeetle and associated ransomware groups underscore the evolving tactics of cybercriminals targeting businesses worldwide. Organizations are urged to strengthen their cybersecurity measures, keep systems updated with the latest patches, and remain vigilant against sophisticated ransomware attacks that employ advanced evasion techniques.
About ESET
ESET is a global cybersecurity company providing cutting-edge solutions and services to protect businesses and consumers from increasingly sophisticated digital threats. With over 30 years of experience, ESET offers comprehensive security solutions that combine advanced technology with human expertise.