Mustang Panda Enhances Malware Arsenal to Spy on Asia-Pacific Governments
Cybersecurity firm Trend Micro has uncovered significant advancements in the malware arsenal of the threat actor known as Mustang Panda. Operating under the moniker Earth Preta, Mustang Panda has refined its tools to facilitate data exfiltration and deploy next-stage payloads, intensifying its cyber espionage efforts against government entities in the Asia-Pacific (APAC) region.
Expansion of Malware Tools
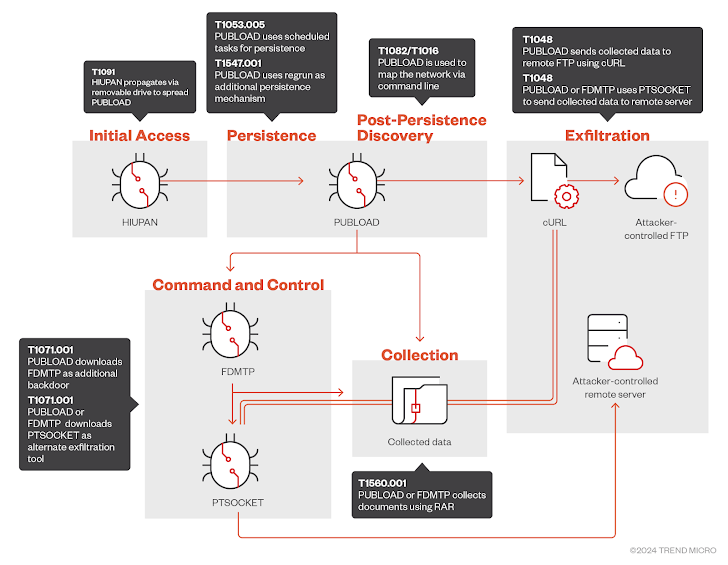
Trend Micro observed the propagation of PUBLOAD via a variant of the worm HIUPAN. PUBLOAD is a known downloader malware linked to Mustang Panda since early 2022. It has been used in cyber attacks targeting government entities across the APAC region to deliver the notorious PlugX malware.
According to security researchers Lenart Bermejo, Sunny Lu, and Ted Lee, “PUBLOAD was also used to introduce supplemental tools into the targets’ environment, such as FDMTP to serve as a secondary control tool, which was observed to perform similar tasks as that of PUBLOAD; and PTSOCKET, a tool used as an alternative exfiltration option.”
Propagation Techniques
Mustang Panda’s utilization of removable drives as a propagation vector for HIUPAN was previously documented by Trend Micro in March 2023. The threat actor is also tracked by Google-owned Mandiant as MISTCLOAK, observed in connection with a cyber espionage campaign targeting the Philippines that may have commenced as far back as September 2021.
PUBLOAD is equipped with features to conduct reconnaissance of infected networks and harvest files of interest, including documents and presentations (.doc, .docx, .xls, .xlsx, .pdf, .ppt, and .pptx). It also serves as a conduit for a new hacking tool dubbed FDMTP, described as a “simple malware downloader” implemented based on TouchSocket over Duplex Message Transport Protocol (DMTP).
Captured information is compressed into an RAR archive and exfiltrated to an attacker-controlled FTP site via cURL. Alternatively, Mustang Panda has been observed deploying a custom program named PTSOCKET, capable of transferring files in multi-thread mode to expedite data theft.
Advanced Malware Deployment
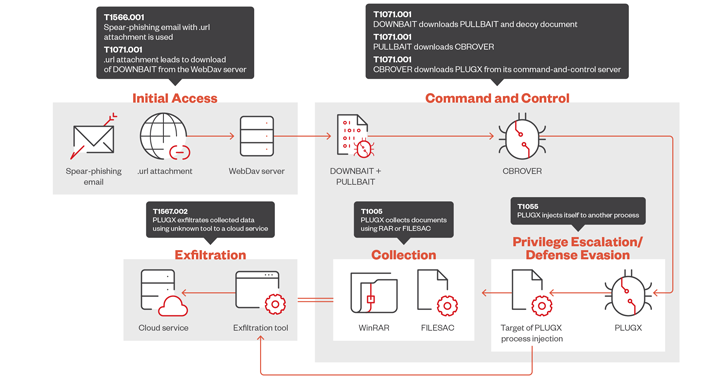
Further insights from Trend Micro attribute the adversary to a “fast-paced” spear-phishing campaign detected in June 2024. This campaign distributed email messages containing a .url attachment, which, when launched, delivers a signed downloader dubbed DOWNBAIT.
The campaign is believed to have targeted countries including Myanmar, the Philippines, Vietnam, Singapore, Cambodia, and Taiwan, based on the filenames and content of the decoy documents used.
DOWNBAIT acts as a first-stage loader tool used to retrieve and execute the PULLBAIT shellcode in memory. This shellcode subsequently downloads and runs the first-stage backdoor referred to as CBROVER.
Escalated Threat Activities
The CBROVER implant supports file download and remote shell execution capabilities. It also functions as a delivery vehicle for the PlugX remote access trojan (RAT). PlugX then deploys another bespoke file collector called FILESAC, designed to collect and exfiltrate the victim’s files.
The disclosure of these activities comes as Palo Alto Networks Unit 42 detailed Mustang Panda’s abuse of Visual Studio Code’s embedded reverse shell feature to gain a foothold in target networks. This indicates that the threat actor is actively tweaking its modus operandi to enhance its espionage capabilities.
Conclusion
“Earth Preta has shown significant advancements in their malware deployment and strategies, particularly in their campaigns targeting government entities,” the researchers noted. “The group has evolved their tactics, leveraging multi-stage downloaders (from DOWNBAIT to PlugX) and possibly exploiting Microsoft’s cloud services for data exfiltration.”
The continued evolution of Mustang Panda’s tools and techniques underscores the escalating threat posed by sophisticated cyber espionage groups targeting critical government infrastructure in the Asia-Pacific region. Organizations are advised to strengthen their cybersecurity defenses and remain vigilant against such advanced persistent threats.



