Blind Eagle Targets Colombian Insurance Sector with Customized Quasar RAT
A threat actor known as Blind Eagle has been targeting the Colombian insurance sector since June 2024 with a customized version of the Quasar Remote Access Trojan (RAT). Blind Eagle, also referred to as AguilaCiega, APT-C-36, and APT-Q-98, has previously focused its cyber espionage activities on organizations and individuals in South America, particularly those within government and finance sectors in Colombia and Ecuador.
Phishing Emails and Tax Authority Impersonation
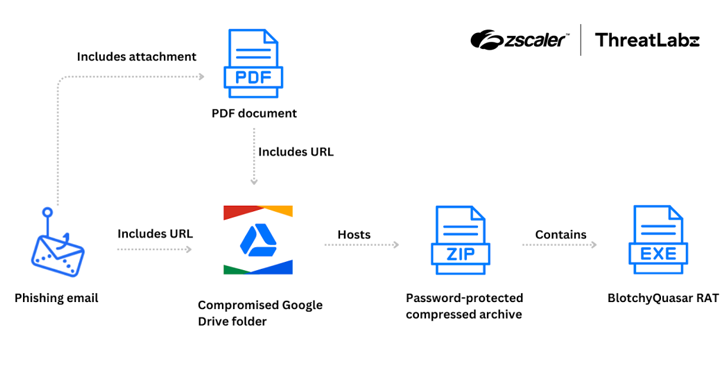
According to Zscaler ThreatLabz researcher Gaetano Pellegrino, the attack campaign starts with phishing emails impersonating the Colombian tax authority. These emails are designed to create a sense of urgency by claiming that the recipient owes unpaid taxes, threatening legal action or property seizure to compel the victim to act quickly.
The phishing emails either include malicious links embedded in PDF attachments or directly within the email body. These links lead to ZIP archives hosted on Google Drive accounts belonging to compromised regional government organizations in Colombia.
Customized Quasar RAT: BlotchyQuasar
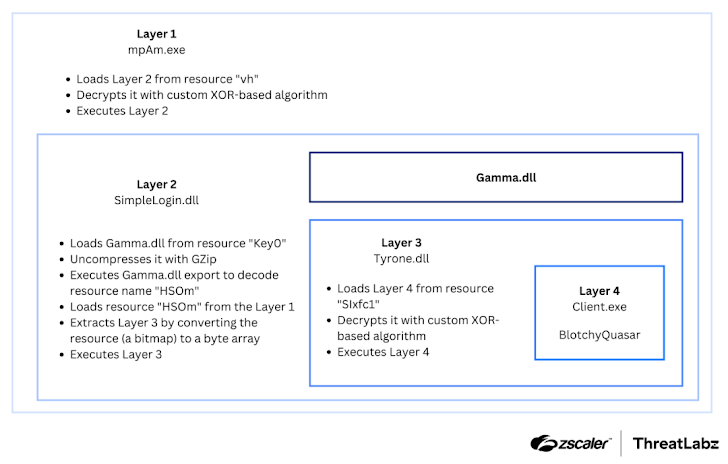
The downloaded ZIP archive contains a modified version of Quasar RAT, dubbed BlotchyQuasar, which has been enhanced with additional layers of obfuscation using tools like DeepSea or ConfuserEx. These techniques are designed to make the malware more difficult to analyze and reverse-engineer, allowing it to evade detection for longer periods.
Once installed, BlotchyQuasar provides attackers with a wide range of capabilities, including:
- Keystroke logging to capture sensitive information.
- Shell command execution for deeper system control.
- Data theft from web browsers and FTP clients.
- Monitoring interactions with banking and payment services, particularly in Colombia and Ecuador.
Command-and-Control (C2) Infrastructure
Blind Eagle uses a sophisticated command-and-control (C2) infrastructure that leverages Pastebin as a dead-drop resolver to retrieve the C2 domain. The group also uses Dynamic DNS (DDNS) services to host the C2 domain, and shields its infrastructure behind VPN nodes and compromised routers, primarily located in Colombia. This setup enables the attackers to maintain a high level of operational security, making it difficult for authorities to trace their activities.
Conclusion
Blind Eagle’s continued targeting of the Colombian insurance sector with customized malware highlights the group’s persistent focus on South American organizations. The use of phishing tactics, coupled with a highly customized version of Quasar RAT, showcases the evolving nature of the group’s attacks and their ability to adapt to security measures.
As this campaign continues, organizations, particularly in Colombia and Ecuador, are advised to remain vigilant, implement strong email security measures, and ensure that employees are aware of phishing tactics designed to exploit urgency and fear.




