Chinese Hackers Exploit Visual Studio Code in Southeast Asian Cyberattacks
The China-linked advanced persistent threat (APT) group known as Mustang Panda has been observed leveraging Visual Studio Code as part of a cyber espionage campaign targeting government entities in Southeast Asia. This group, operational since 2012, is known for its extensive cyberattacks, particularly against governmental and religious organizations across Europe and Asia, with a focus on South China Sea countries.
Weaponizing Visual Studio Code
In this latest campaign, Mustang Panda abused Visual Studio Code’s embedded reverse shell to infiltrate networks and execute arbitrary code. This relatively new technique was first demonstrated in September 2023 and now plays a critical role in Mustang Panda’s toolkit for breaching systems.
According to a report from Palo Alto Networks Unit 42 researcher Tom Fakterman, the group used Visual Studio Code’s reverse shell feature to gain access to their targets. Attackers either use the portable version of Visual Studio Code or an already installed version on the victim’s machine. By running the command code.exe tunnel, they gain access to a Visual Studio Code web environment, enabling them to issue commands and manipulate the system remotely after authenticating through GitHub.
Broader Implications of the Attack
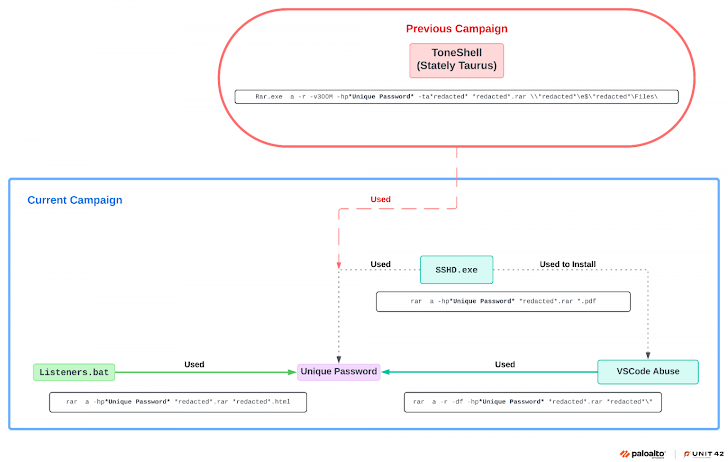
The campaign against Southeast Asian governments is considered a continuation of similar activities targeting the region, including attacks in late 2023. Mustang Panda’s use of Visual Studio Code to establish a foothold in target systems is a significant evolution in its methods, highlighting how APTs are increasingly weaponizing common software tools to avoid detection.
Once inside, the group performed reconnaissance, exfiltrated sensitive data, and used OpenSSH to execute commands and spread laterally within networks. Further analysis revealed the presence of ShadowPad malware, a powerful backdoor used by several Chinese espionage groups.
ShadowPad and Multiple Intrusion Clusters
In an interesting twist, forensic evidence suggested two simultaneous intrusion clusters within the compromised environments, some of which occurred on the same endpoints. The second cluster involved ShadowPad, a modular backdoor often shared among Chinese APT groups, raising the possibility of collaboration or piggybacking between different threat actors.
While it’s unclear if both clusters are linked, researchers from Unit 42 noted that Stately Taurus (another Chinese APT group) could be responsible for both, or the two groups could be coordinating their attacks.
Conclusion
The use of Visual Studio Code as an attack vector highlights the evolving tactics of APT groups like Mustang Panda. This campaign shows how attackers can weaponize legitimate software to infiltrate critical infrastructure, making the detection and mitigation of these attacks increasingly complex. Organizations, particularly in Southeast Asia, must bolster their defenses against these sophisticated espionage campaigns to protect sensitive data and infrastructure from future threats.