TIDRONE Espionage Group Targets Taiwan Drone Manufacturers in Cyber Campaign

A newly identified threat actor, dubbed TIDRONE, has emerged in 2024, targeting drone manufacturers in Taiwan as part of a suspected espionage campaign. Trend Micro researchers have linked the group’s activities to Chinese-speaking threat actors, particularly given the focus on Taiwan’s military-related industry supply chains.
Espionage Focus on Taiwan’s Drone Industry
TIDRONE has demonstrated a keen interest in Taiwan’s drone manufacturing sector, likely due to the strategic importance of drones in military and defense operations. Although the exact method used by TIDRONE to gain initial access to its targets remains unclear, the group has deployed custom malware and remote desktop tools to infiltrate and compromise systems.
Key Malware Used: CXCLNT and CLNTEND
The group utilizes two key malware variants in its attacks:
- CXCLNT: This malware has capabilities for uploading and downloading files, collecting system information, and wiping traces of its presence. It is primarily used to establish initial control over compromised systems and facilitate further infiltration.
- CLNTEND: Discovered in April 2024, CLNTEND is a more advanced remote access tool (RAT) that supports various network protocols, including TCP, HTTP, HTTPS, TLS, and SMB. This flexibility makes it a powerful tool for long-term access and data exfiltration.
Potential Supply Chain Attack Vector
An interesting detail from Trend Micro’s analysis is the discovery that many of the victims used the same enterprise resource planning (ERP) software, raising concerns about the possibility of a supply chain attack. This tactic would allow TIDRONE to compromise multiple organizations through a shared software vulnerability.
Three-Stage Attack Process
TIDRONE’s attack process unfolds in three stages:
- Privilege Escalation: The group bypasses User Account Control (UAC) to gain elevated access.
- Credential Dumping: TIDRONE retrieves sensitive login credentials to move laterally within compromised networks.
- Defense Evasion: Antivirus products are disabled to prevent detection and allow uninterrupted malware operations.
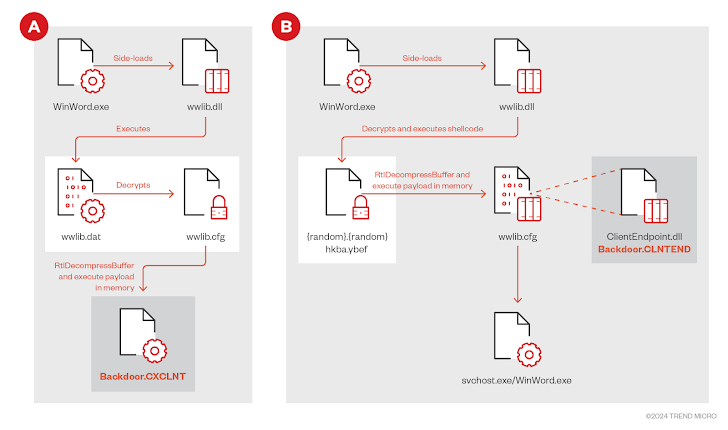
DLL Sideloading and Microsoft Word Exploitation
TIDRONE’s malware is sideloaded through malicious DLL files via Microsoft Word, providing the threat actors access to sensitive information, including system file listings and computer names. The malware also clears traces of the intrusion while downloading additional payloads for further exploitation.
Chinese-Speaking Threat Actor Attribution
Trend Micro researchers Pierre Lee and Vickie Su suggest that TIDRONE’s campaign shares similarities with other Chinese espionage-related activities. The consistency in file compilation times and the operation period align with known Chinese-speaking threat actor patterns, leading to the assessment that this is likely a yet-unidentified Chinese threat group.
Conclusion
The TIDRONE group’s campaign against Taiwan’s drone manufacturers demonstrates the growing threat of cyber espionage in the military and defense sectors. The use of custom malware, potential supply chain attacks, and the exploitation of critical industries highlights the importance of heightened cybersecurity defenses in these fields. As TIDRONE continues to operate, organizations must remain vigilant and prioritize securing their supply chains and sensitive systems from sophisticated cyber threats.




