Typosquatting in GitHub Actions: A New Supply Chain Attack Risk for Developers
Typosquatting, a long-standing threat in cybersecurity, has now found its way into GitHub Actions, exposing developers to hidden malicious code that could compromise entire software supply chains. By exploiting minor typographical errors in GitHub workflows, attackers can inject malicious actions into repositories, running harmful code without the developer’s knowledge.
Understanding Typosquatting in Software Development
Typosquatting typically involves registering domains or packages with names that closely resemble legitimate ones, relying on users making small typing errors. This technique has been a common method for cybercriminals to deceive users into visiting malicious websites or downloading booby-trapped packages. Typosquatting attacks have been used across popular package management platforms such as PyPI, npm, Maven Central, NuGet, RubyGems, and Crate, targeting developers through these open-source repositories.
Now, new research from cloud security firm Orca reveals that even GitHub Actions, a platform used for Continuous Integration and Continuous Delivery (CI/CD), is susceptible to this threat.
The GitHub Actions Typosquatting Attack
GitHub Actions enables developers to automate workflows such as testing, building, and deploying code. However, if a developer accidentally types an incorrect name when invoking an action, they may trigger a malicious one registered by attackers.
According to security researcher Ofir Yakobi, who shared findings with The Hacker News, all an attacker needs to do is create an organization or repository with a name similar to a popular GitHub Action. If a developer unknowingly references the misspelled version, the attacker’s malicious action will run within the repository’s context. This can lead to several severe consequences:
- Source Code Tampering: Attackers can modify the code within the repository.
- Data Theft: Sensitive information, such as API keys or credentials, can be exfiltrated.
- Malware Deployment: Attackers can push malicious code through the workflow.
- Wider Organizational Impact: Attackers may use the developer’s GitHub credentials to push changes to other repositories within the same organization, extending the damage across multiple projects.
Real-World Example of Typosquatting in GitHub
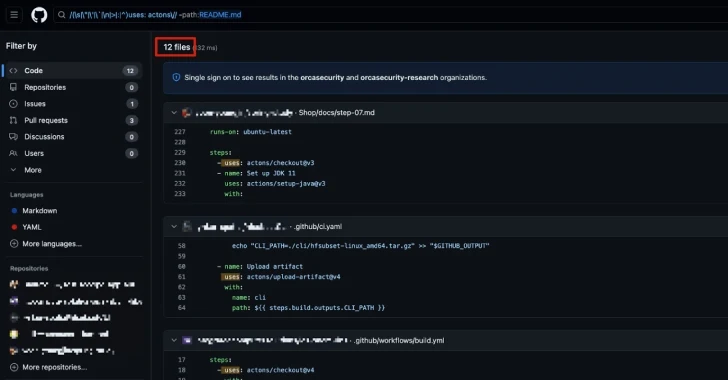
Orca’s research uncovered 198 GitHub files where developers mistakenly invoked “action/checkout” or “actons/checkout” instead of the correct “actions/checkout” (missing “s” or “i”). These minor errors place the affected projects at risk of running malicious code if attackers register these similarly named actions.
This technique is attractive to cybercriminals due to its low cost and high potential impact, especially in the context of CI/CD workflows. By targeting GitHub Actions, attackers can infiltrate software projects, which may then affect numerous downstream users and customers through compromised builds and deployments.
Mitigating the Risk of Typosquatting in GitHub Actions
To protect against typosquatting attacks in GitHub Actions, developers must remain vigilant. Key steps include:
- Double-check Action Names: Always verify that the correct GitHub Action and organization are being referenced in workflows.
- Stick to Trusted Sources: Only use GitHub Actions from well-established and reputable sources.
- Scan CI/CD Workflows: Periodically review workflows for any potential typosquatting risks.
- Enable Security Best Practices: Use security features like GitHub’s Dependabot to detect vulnerabilities and implement tools that scan for misconfigurations.
Broader Implications for Software Supply Chains
Typosquatting in GitHub Actions is a stark reminder of the broader risks to software supply chains. Attackers are increasingly exploiting developer workflows as entry points to spread malware and compromise downstream projects. The simplicity and ease with which these attacks can occur make them particularly dangerous, especially when unnoticed within CI/CD pipelines.
While this research highlights the risks present in public repositories, the threat to private repositories remains an even larger concern. Errors in private workflows may lead to significant security breaches that are harder to detect and mitigate.
Conclusion: Proactive Vigilance in CI/CD Security
This discovery by Orca illustrates how a seemingly minor mistake in a GitHub Action can lead to catastrophic consequences, not just for individual developers but for entire organizations and their software ecosystems. Vigilance, coupled with strong security practices, is essential to prevent attackers from exploiting these weaknesses.
Developers and organizations must take a proactive approach to secure their CI/CD pipelines by carefully scrutinizing action names and implementing protective measures against software supply chain attacks. As the landscape of cybersecurity threats evolves, so must the tools and practices to safeguard modern software development environments.




