North Korean Threat Actors Exploit LinkedIn Job Scams to Deploy COVERTCATCH Malware
In a concerning new trend, North Korean-affiliated cybercriminals are weaponizing LinkedIn to target developers as part of a broader job recruitment scam. These sophisticated phishing operations, which aim to infiltrate systems through fake job offers, have been particularly focused on professionals within the Web3 sector, according to cybersecurity firm Mandiant, a subsidiary of Google.
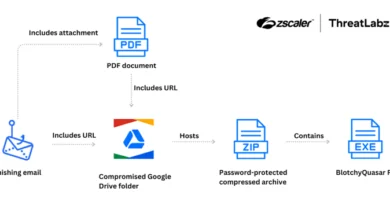
One of the primary tactics observed involves sending unsuspecting victims coding challenges, which serve as the initial infection vector. Researchers Robert Wallace, Blas Kojusner, and Joseph Dobson of Mandiant detailed an incident where hackers used a Python coding test to disguise a ZIP file containing the COVERTCATCH malware.
Once the malicious file is opened, the malware initiates a secondary payload specifically designed to target macOS systems, establishing persistence through Launch Agents and Launch Daemons. This foothold allows the attackers to control the system remotely and initiate further stages of the attack.
This job-themed malware delivery method isn’t new for North Korean hacking groups. It bears similarities to previous campaigns such as “Operation Dream Job” and “Contagious Interview,” which also utilized fake job offers to lure victims into downloading malicious software. These decoy recruitment efforts have delivered other malware families like RustBucket and KANDYKORN, further highlighting the diversity of North Korea’s cyber arsenal.
Mandiant uncovered another instance of this social engineering tactic where hackers sent a PDF masquerading as a job description for a “VP of Finance and Operations” at a leading cryptocurrency exchange. The attached file unleashed RustBucket, a backdoor written in Rust, that enables attackers to execute files, harvest system information, and maintain persistence by masquerading as a Safari update.
Broader Implications for Web3 and Cryptocurrency Firms
North Korea’s cyber-operations have extended beyond phishing attacks to include software supply chain compromises, as seen in high-profile incidents involving 3CX and JumpCloud. These attacks often start with malware infiltration, after which the hackers pivot to sensitive areas of a company’s infrastructure. By targeting password managers and code repositories, they gather credentials and key information necessary to access hot wallets, enabling them to drain funds from cryptocurrency exchanges.
The sophistication of these operations has drawn attention from major security agencies. The FBI recently issued a warning highlighting North Korean threat actors’ focus on the cryptocurrency sector. Using “highly tailored, difficult-to-detect social engineering campaigns,” these attackers often impersonate recruitment firms or industry professionals to establish a false sense of trust. Once contact is made, the hackers meticulously engage with their targets to increase the legitimacy of the interaction, often spending significant time to build familiarity and trust before delivering malware.
The Long Game: Social Engineering and Pre-Operational Research
A key component of these operations is the extensive research conducted on the targets prior to initial contact. Cybercriminals gather personal and professional details, from affiliations and interests to personal relationships and events, which they then use to personalize their phishing attempts. This tailored approach significantly increases the success rate of the attacks, as victims are more likely to engage with offers that appear highly relevant to their personal or professional interests.
The implications of these ongoing campaigns are alarming. With the Web3 sector and cryptocurrency markets at the center of these attacks, the potential for financial loss and data compromise is vast. The revenue generated from these cyber heists is believed to directly fund North Korea’s state activities, as the country faces stringent international sanctions.
Conclusion: Strengthening Defenses Against Social Engineering Attacks
The persistent threat posed by North Korean cyber actors underscores the importance of robust cybersecurity measures, especially within sectors like Web3 and cryptocurrency that are prime targets for sophisticated social engineering campaigns. As these threat actors continue to evolve their tactics, businesses must remain vigilant, educating employees about phishing schemes, conducting regular security audits, and implementing strong authentication measures to safeguard against such attacks.
North Korea’s brazen and highly tailored approach to hacking highlights the evolving nature of cyber threats, emphasizing the need for proactive defenses in an increasingly digital world.